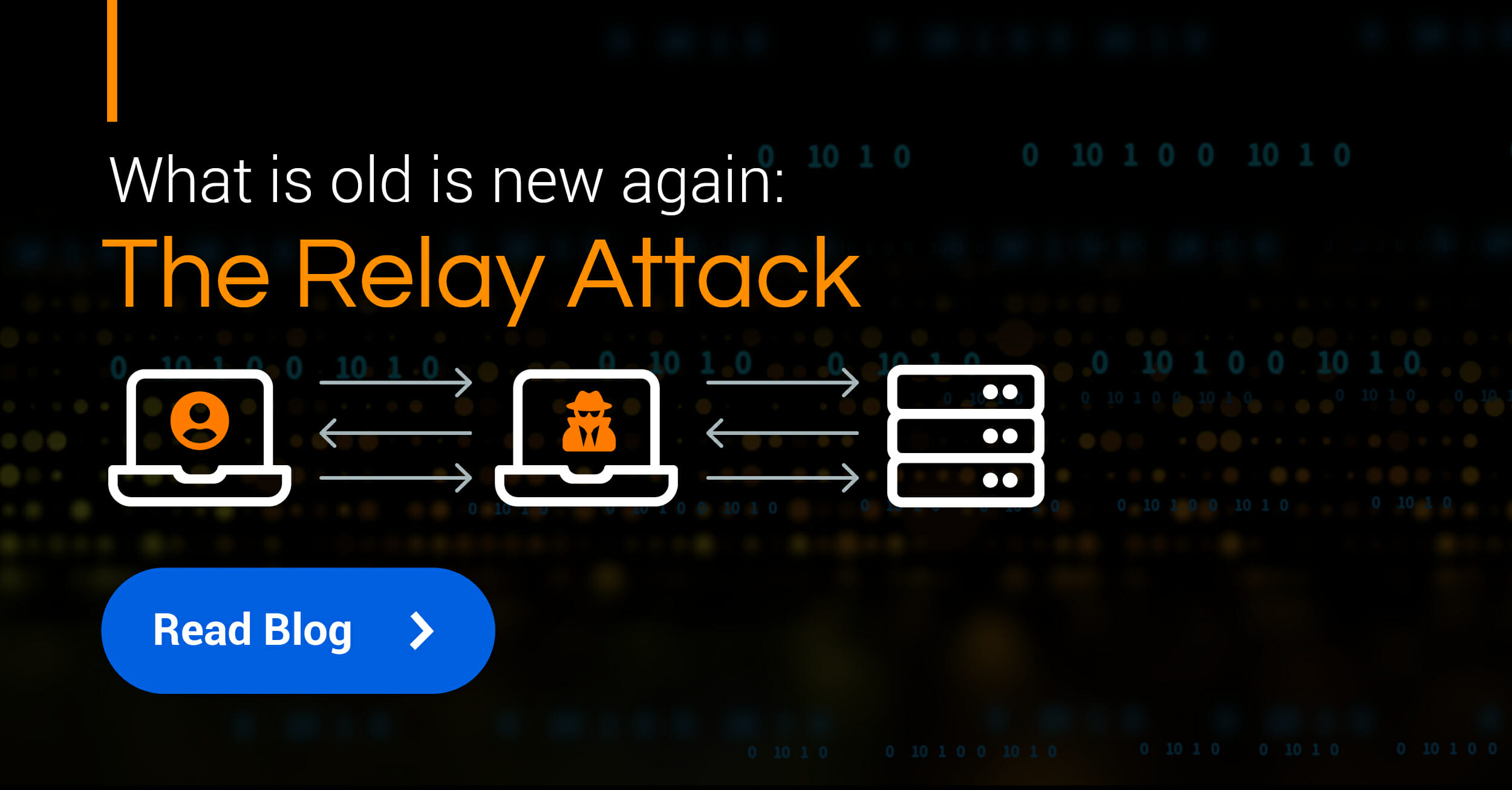
What Is A Relay Attack Device . In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or. In the past, thieves found success using what’s known as a relay attack. To help describe a relay attack, it’s common to first explain how a man in the middle(mitm) attack works: One stands by the targeted vehicle, while the other stands near the house with a device. These hacks amplify the signal between the car and. A relay attack usually involves two people working together. A car relay attack is a form of wireless theft that exploits keyless entry systems in modern vehicles.
from www.secureauth.com
In the past, thieves found success using what’s known as a relay attack. One stands by the targeted vehicle, while the other stands near the house with a device. These hacks amplify the signal between the car and. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or. To help describe a relay attack, it’s common to first explain how a man in the middle(mitm) attack works: A relay attack usually involves two people working together. A car relay attack is a form of wireless theft that exploits keyless entry systems in modern vehicles.
What is old is new again The Relay Attack SecureAuth
What Is A Relay Attack Device A car relay attack is a form of wireless theft that exploits keyless entry systems in modern vehicles. These hacks amplify the signal between the car and. In the past, thieves found success using what’s known as a relay attack. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or. A car relay attack is a form of wireless theft that exploits keyless entry systems in modern vehicles. To help describe a relay attack, it’s common to first explain how a man in the middle(mitm) attack works: A relay attack usually involves two people working together. One stands by the targeted vehicle, while the other stands near the house with a device.
From www.autoconnectedcar.com
Warning Double Device Relay Key Fob System Hack for Thieves to Steal What Is A Relay Attack Device In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or. A car relay attack is a form of wireless theft that exploits keyless entry systems in modern vehicles. A relay attack usually involves two people working together. These hacks amplify the signal between the car and. To help. What Is A Relay Attack Device.
From www.researchgate.net
The relay attack in practice (a) opening the door with the relay. (b What Is A Relay Attack Device One stands by the targeted vehicle, while the other stands near the house with a device. In the past, thieves found success using what’s known as a relay attack. A car relay attack is a form of wireless theft that exploits keyless entry systems in modern vehicles. A relay attack usually involves two people working together. In a relay attack,. What Is A Relay Attack Device.
From www.fleetaccess.nl
Wat is relay attack? En hoe beveilig ik de auto daartegen? What Is A Relay Attack Device A car relay attack is a form of wireless theft that exploits keyless entry systems in modern vehicles. One stands by the targeted vehicle, while the other stands near the house with a device. In the past, thieves found success using what’s known as a relay attack. A relay attack usually involves two people working together. To help describe a. What Is A Relay Attack Device.
From edu.svet.gob.gt
Relay Attack Real Device! Car Theft With DIY Repeater What Is A Relay Attack Device In the past, thieves found success using what’s known as a relay attack. A relay attack usually involves two people working together. To help describe a relay attack, it’s common to first explain how a man in the middle(mitm) attack works: In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob,. What Is A Relay Attack Device.
From www.bayareaaudiovisions.com
Automobile Thefts What Is a Relay Attack? What Is A Relay Attack Device A relay attack usually involves two people working together. To help describe a relay attack, it’s common to first explain how a man in the middle(mitm) attack works: In the past, thieves found success using what’s known as a relay attack. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob,. What Is A Relay Attack Device.
From ncd.io
Key Fob Relays Handheld Remote Control of Electronics What Is A Relay Attack Device One stands by the targeted vehicle, while the other stands near the house with a device. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or. A relay attack usually involves two people working together. To help describe a relay attack, it’s common to first explain how a. What Is A Relay Attack Device.
From www.semanticscholar.org
Figure 1 from Vehicle Relay Attack Avoidance Methods Using RF Signal What Is A Relay Attack Device These hacks amplify the signal between the car and. A car relay attack is a form of wireless theft that exploits keyless entry systems in modern vehicles. To help describe a relay attack, it’s common to first explain how a man in the middle(mitm) attack works: One stands by the targeted vehicle, while the other stands near the house with. What Is A Relay Attack Device.
From www.auto-grab.com
Keyless go repeater Starter Kits for 3 uses Relay attack device for 3 What Is A Relay Attack Device A relay attack usually involves two people working together. To help describe a relay attack, it’s common to first explain how a man in the middle(mitm) attack works: In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or. In the past, thieves found success using what’s known as. What Is A Relay Attack Device.
From www.intechopen.com
Implementation of a Countermeasure to Relay Attacks for Contactless HF What Is A Relay Attack Device A relay attack usually involves two people working together. To help describe a relay attack, it’s common to first explain how a man in the middle(mitm) attack works: These hacks amplify the signal between the car and. One stands by the targeted vehicle, while the other stands near the house with a device. A car relay attack is a form. What Is A Relay Attack Device.
From www.youtube.com
DIY Controlling AC Devices by 5V Relay YouTube What Is A Relay Attack Device One stands by the targeted vehicle, while the other stands near the house with a device. These hacks amplify the signal between the car and. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or. A car relay attack is a form of wireless theft that exploits keyless. What Is A Relay Attack Device.
From www.slideserve.com
PPT Keep Your Enemies Close Distance Bounding Against Smartcard What Is A Relay Attack Device In the past, thieves found success using what’s known as a relay attack. To help describe a relay attack, it’s common to first explain how a man in the middle(mitm) attack works: One stands by the targeted vehicle, while the other stands near the house with a device. A car relay attack is a form of wireless theft that exploits. What Is A Relay Attack Device.
From unlockcarsgrabber.com
Keyless Go Repeater FBS4 Relay Attack UnlockCars Grabber What Is A Relay Attack Device In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or. One stands by the targeted vehicle, while the other stands near the house with a device. These hacks amplify the signal between the car and. In the past, thieves found success using what’s known as a relay attack.. What Is A Relay Attack Device.
From opposite-lock.com
How to reduce the odds of your car being stolen Come for the cars What Is A Relay Attack Device One stands by the targeted vehicle, while the other stands near the house with a device. To help describe a relay attack, it’s common to first explain how a man in the middle(mitm) attack works: In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or. A relay attack. What Is A Relay Attack Device.
From howcarspecs.blogspot.com
Relay Attack Device How Car Specs What Is A Relay Attack Device These hacks amplify the signal between the car and. In the past, thieves found success using what’s known as a relay attack. A relay attack usually involves two people working together. In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or. To help describe a relay attack, it’s. What Is A Relay Attack Device.
From www.bayareaaudiovisions.com
Automobile Thefts What Is a Relay Attack? What Is A Relay Attack Device A car relay attack is a form of wireless theft that exploits keyless entry systems in modern vehicles. A relay attack usually involves two people working together. These hacks amplify the signal between the car and. One stands by the targeted vehicle, while the other stands near the house with a device. In a relay attack, malicious actors intercept and. What Is A Relay Attack Device.
From www.which.co.uk
Keyless car theft why aren't car manufacturers doing more? Which? News What Is A Relay Attack Device These hacks amplify the signal between the car and. To help describe a relay attack, it’s common to first explain how a man in the middle(mitm) attack works: In a relay attack, malicious actors intercept and relay signals between a legitimate device (such as a key fob, payment card, or. A relay attack usually involves two people working together. One. What Is A Relay Attack Device.
From www.youtube.com
Car Security gadgets UNBOXED! Key Fob Relay Attack! YouTube What Is A Relay Attack Device These hacks amplify the signal between the car and. One stands by the targeted vehicle, while the other stands near the house with a device. A car relay attack is a form of wireless theft that exploits keyless entry systems in modern vehicles. To help describe a relay attack, it’s common to first explain how a man in the middle(mitm). What Is A Relay Attack Device.
From howcarspecs.blogspot.com
Relay Attack Device How Car Specs What Is A Relay Attack Device These hacks amplify the signal between the car and. In the past, thieves found success using what’s known as a relay attack. A car relay attack is a form of wireless theft that exploits keyless entry systems in modern vehicles. One stands by the targeted vehicle, while the other stands near the house with a device. In a relay attack,. What Is A Relay Attack Device.